1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
|
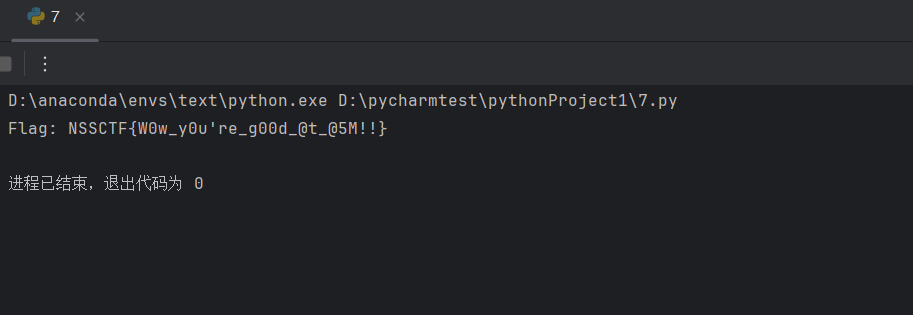
def do2_swap_bytes(data1, bx, di):
for _ in range(4):
temp = data1[bx]
data1[bx] = data1[di]
data1[di] = temp
bx += 1
di += 1
def do1_modify_data1(data1_initial):
data1 = list(data1_initial) # Make a mutable copy
si = 0
for _ in range(8):
di = si + 4
if di >= 28:
di -= 28
bx = si
do2_swap_bytes(data1, bx, di)
si += 4
return bytes(data1)
def reverse_enc(data2, modified_data1):
flag = bytearray()
si = 0
di = 0
for _ in range(8):
ax_word1 = (modified_data1[di + 2] << 8) | modified_data1[di + 1]
flag_word1 = ((data2[si+1] << 8) | data2[si]) ^ ax_word1
flag.append(flag_word1 & 0xFF)
flag.append((flag_word1 >> 8) & 0xFF)
ax_word2 = (modified_data1[di + 3] << 8) | modified_data1[di + 2] # Note: should be di+3, di+2 for word
flag_word2 = ((data2[si+3] << 8) | data2[si+2]) ^ ax_word2
flag.append(flag_word2 & 0xFF)
flag.append((flag_word2 >> 8) & 0xFF)
si += 4
di += 4
return bytes(flag)
DATA1_INITIAL = bytes([0x26, 0x27, 0x24, 0x25, 0x2A, 0x2B, 0x28, 0x00,
0x2E, 0x2F, 0x2C, 0x2D, 0x32, 0x33, 0x30, 0x00,
0x36, 0x37, 0x34, 0x35, 0x3A, 0x3B, 0x38, 0x39,
0x3E, 0x3F, 0x3C, 0x3D, 0x3F, 0x27, 0x34, 0x11])
DATA2 = bytes([0x69, 0x77, 0x77, 0x66, 0x73, 0x72, 0x4F, 0x46,
0x03, 0x47, 0x6F, 0x79, 0x07, 0x41, 0x13, 0x47,
0x5E, 0x67, 0x5F, 0x09, 0x0F, 0x58, 0x63, 0x7D,
0x5F, 0x77, 0x68, 0x35, 0x62, 0x0D, 0x0D, 0x50])
modified_data1 = do1_modify_data1(DATA1_INITIAL)
flag_bytes = reverse_enc(DATA2, modified_data1)
flag = flag_bytes.decode('ascii', errors='ignore') # Try to decode as ASCII, ignore errors for non-printable chars.
print(f"Flag: {flag}")
|